The Problem with Traditional MITRE Maps
Security teams typically face these challenges: Time-Consuming: Manually maintaining MITRE coverage maps across multiple tools takes hours per tool Fragmented: Separate maps for endpoint, SIEM, detection-as-code platforms—no unified view Inaccurate: Maps quickly become outdated as detections changeCotool’s Approach
Automatic Discovery & AI-Powered MITRE Mapping
Detections from connected tools are analyzed and mapped to relevant MITRE ATT&CK techniques using AI:
- Analyzes detection names and descriptions
- Reviews query logic and detection body
- Considers tags and metadata
- Generates confidence scores for each mapping
Unified View
All detections are aggregated into a single MITRE matrix showing coverage across your entire stack
Viewing Your Coverage Map
Navigate to Detections > Coverage Map to see: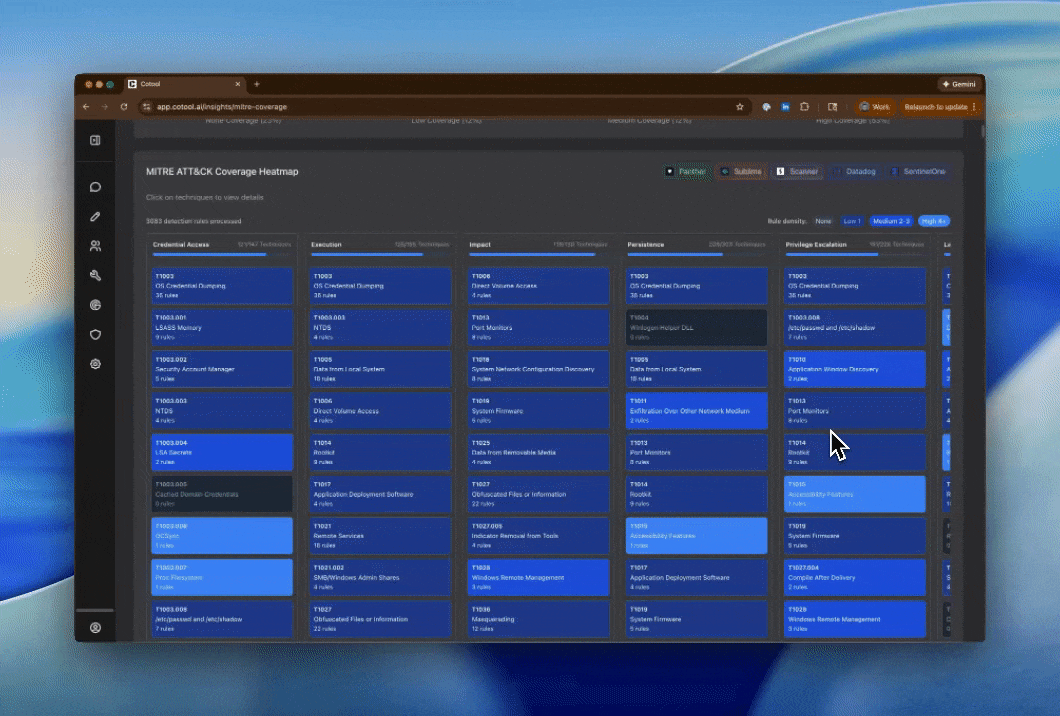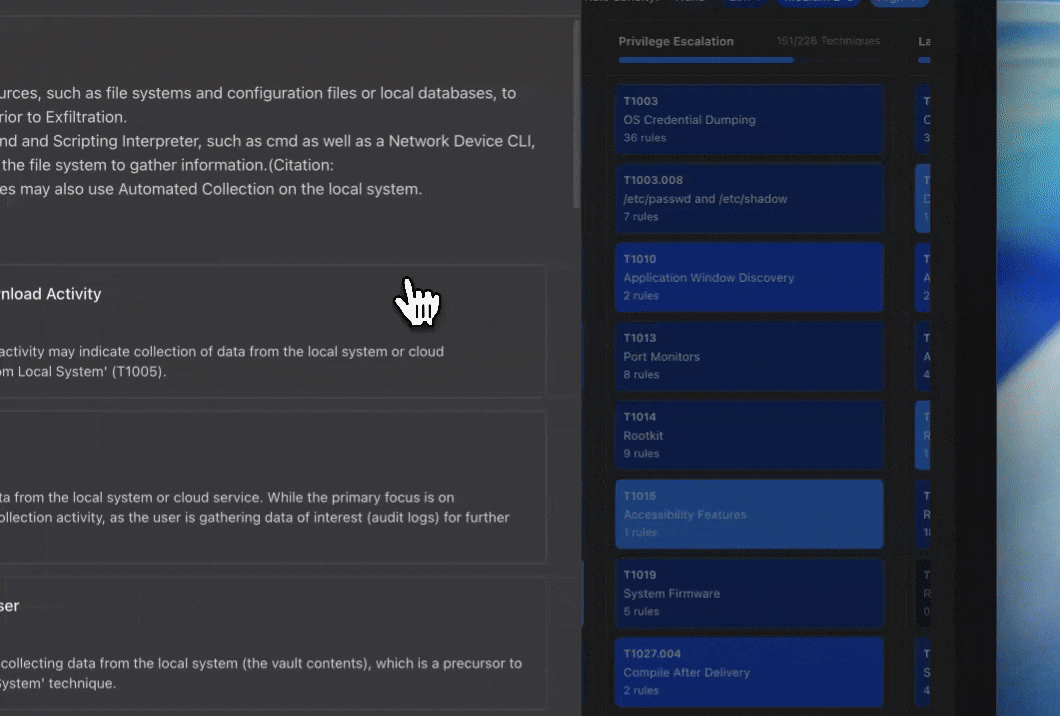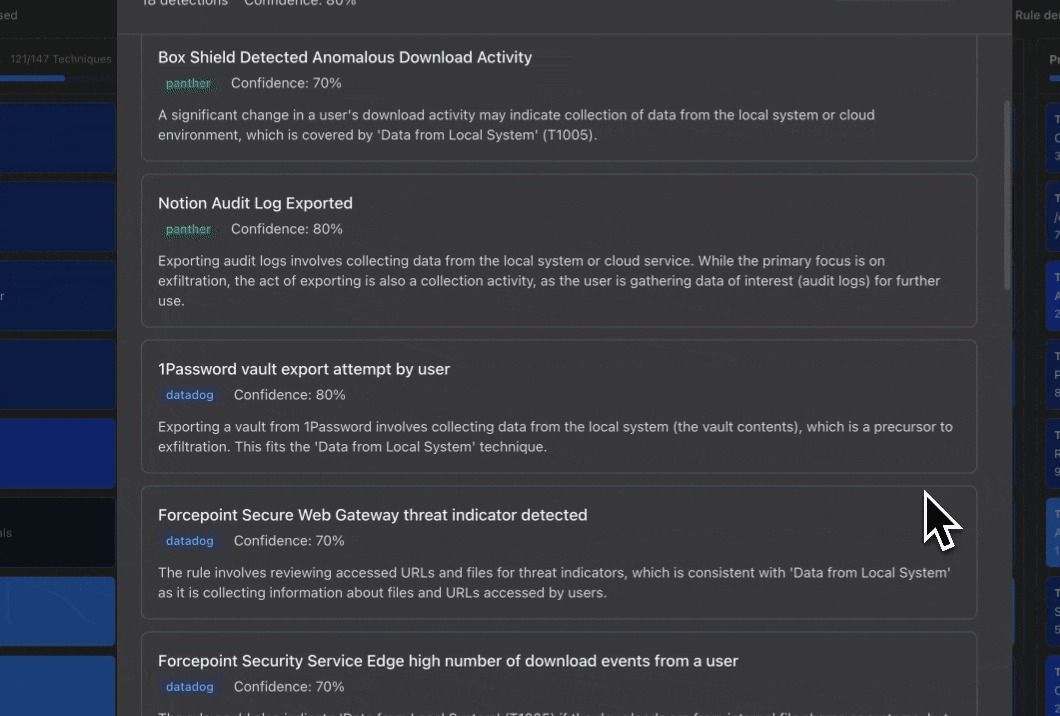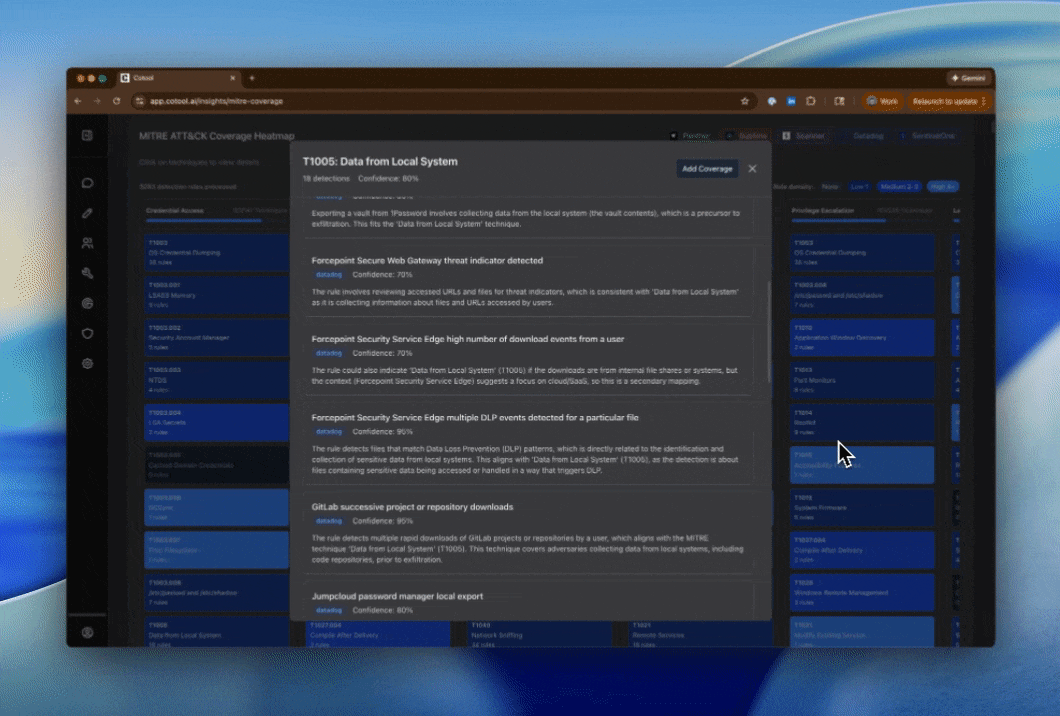
Map Features
The MITRE coverage map shows: Detection Density: Visualize how many detections cover each MITRE technique- Color-coded heatmap showing coverage levels
- Click any technique to see which detections cover it
- Splunk, Datadog, Scanner, Elastic (SIEM/query-based)
- SentinelOne (Endpoint)
- Panther, Sublime (Detection-as-Code)
Understanding Coverage Details
Click on any MITRE technique to see:Detection List
Detection List
All detections covering this technique, showing:
- Detection name
- Source platform (Splunk, Panther, SentinelOne, etc.)
- Confidence score for the mapping
- Reasoning for why it maps to this technique
Detection Details
Detection Details
For each detection, see:
- Platform: Where this detection runs
- Description: What the detection monitors
- Confidence: How strongly it relates to this technique
- Classification Reasoning: Why Cotool mapped it to this technique
- Last Updated: When the classification was performed
Multiple Techniques
Multiple Techniques
A single detection may map to multiple MITRE techniques if it covers multiple attack patterns. Each mapping has its own confidence score.
How the Classification Works
The MITRE classification job runs weekly and:- Fetches detections from all connected platforms
- Analyzes each detection using Cotool to understand what it detects
- Maps to techniques with confidence scores (0-1 scale)
- Validates mappings against the official MITRE ATT&CK framework
- Stores results for visualization in the coverage map
- Detection names and descriptions
- Query/rule logic and body content
- Tags and metadata (including platform-provided MITRE mappings like SentinelOne’s)
- Severity levels and rule types
Frequently Asked Questions
How does Cotool map detections to MITRE techniques?
How does Cotool map detections to MITRE techniques?
Cotool uses AI to analyze each detection’s name, description, query logic, and metadata. Cotool generates mappings to relevant MITRE techniques with confidence scores. For platforms like SentinelOne that provide their own MITRE mappings, Cotool can use those provider-supplied mappings directly.
How often does the map update?
How often does the map update?
The MITRE classification job runs automatically once per week (Sunday at midnight). You can also trigger it manually if you’ve added many new detections and want an immediate update.
What happens to old detections when the job re-runs?
What happens to old detections when the job re-runs?
The classification job is idempotent—it skips detections that have already been classified. Only net-new detections are analyzed and mapped. This makes the weekly job efficient.
Can I manually adjust mappings?
Can I manually adjust mappings?
Currently, mappings are generated automatically by Cotool. If you believe a mapping is incorrect, you may want to improve the detection’s description or metadata to help Cotool classify it more accurately.